Cloud computing adoption has become important for businesses around the world. It provides scalability, flexibility, and cost efficiency. However, these benefits come with unique challenges, especially for Australian businesses operating in large and diverse environments.
Cloud computing has changed the way businesses operate, allowing them to scale operations, reduce costs and improve flexibility. However, the security of data and applications stored in the cloud is a key concern, especially for Australian businesses. With a vast territory, unique regulatory requirements and an ever-changing threat landscape, businesses must adopt appropriate cloud security strategies.
Understanding the Australian Cloud Landscape
Australia’s geographical scale and diverse business landscape pose unique cloud security challenges. The distance between the data center and the user can cause latency issues. Additionally, it is essential to comply with Australia’s strict data privacy regulations, such as the Privacy Act and the Notifiable Data Breaches (NDB) system.

Common Security Threats
Before looking at best practices, it’s important to understand the common security threats facing Australian cloud businesses. These threats include data breaches, unauthorized access, insider threats, and the ever-present risk of data loss.
Best Practices for Cloud Security
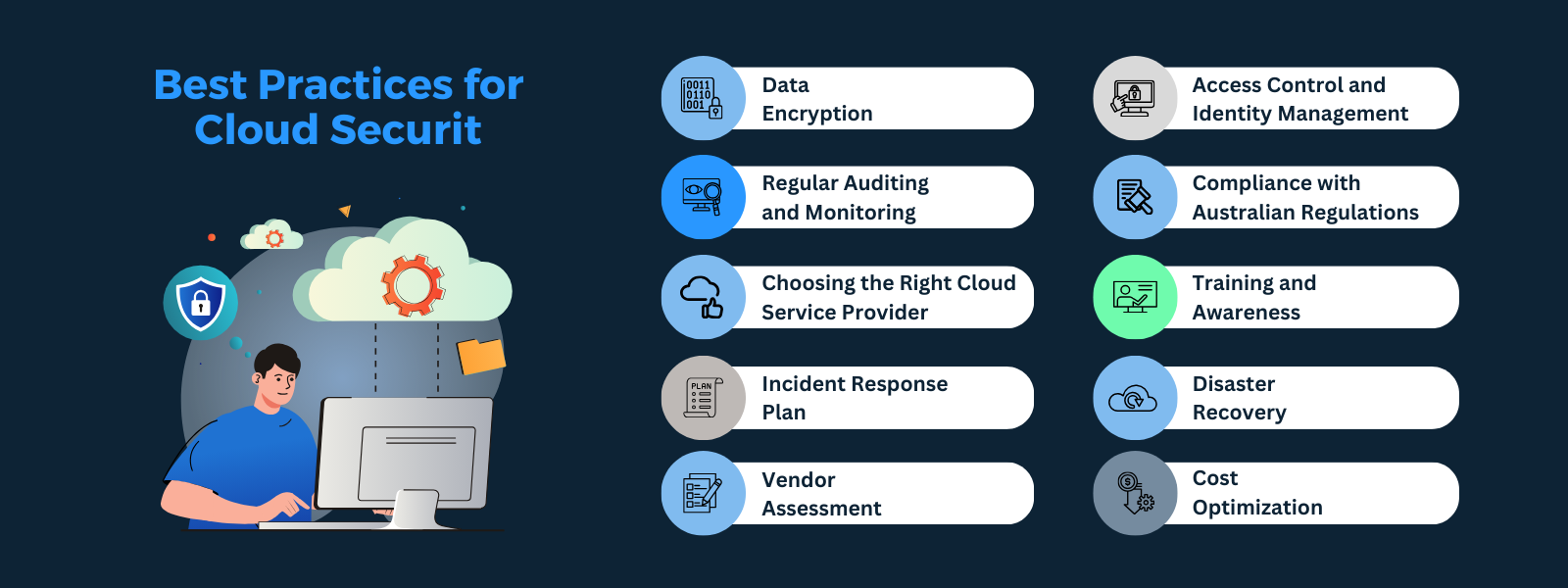
Data Encryption
To protect sensitive data, businesses must implement strong encryption mechanisms. This includes encryption of data at rest and in transit. Encryption ensures that even if data is intercepted, it remains unreadable without the decryption key.
Access Control and Identity Management
Implementing strict access controls and identity management systems is critical. Australian businesses should apply the principle of least privilege, ensuring that only authorized employees have access to specific resources.
Regular Auditing and Monitoring
Continuous testing and monitoring of cloud resources helps detect unusual activities quickly. Anomalies in user behaviour or unauthorized access attempts can be identified and mitigated.
Compliance with Australian Regulations
Compliance with Australian data privacy regulations is non-negotiable. Businesses must ensure that their cloud solutions comply with the Privacy Act, the NDB system and other relevant laws.
Choosing the Right Cloud Service Provider
Choosing a reputable cloud service provider is very important. Australian businesses should evaluate vendors based on their security protocols, compliance certifications and data centre location.
Training and Awareness
Employee training and awareness programs are essential to maintaining a safety-conscious workforce. Educating employees about risks and best practices is a proactive approach to security.

Incident Response Plan
Australian businesses should develop a robust incident response plan to quickly resolve security breaches. Prompt action can minimize potential harm.
Disaster Recovery
Having a disaster recovery plan in place ensures business continuity in the event of unforeseen events. Regular testing and updating is essential to ensure the effectiveness of this plan.
Vendor Assessment
When working with third-party vendors or cloud service providers, Australian businesses should evaluate their security measures and protocols. Weak links can affect overall security.
Cost Optimization
Cloud security doesn’t have to break the bank. Australian businesses should optimize costs by leveraging automation, right-sizing resources and eliminating unnecessary services.

Conclusion
Securing cloud environments is a top priority for businesses. By implementing best practices such as data encryption, access controls and compliance with Australian regulations, organizations can successfully meet the unique challenges of the cloud landscape in Australia. With the right strategies, businesses can enjoy the benefits of cloud computing while protecting their data and operations.
In short, securing cloud environments is not just a choice but a necessity for Australian businesses. By applying the best practices outlined in this article, you can address the unique challenges and securely enjoy the benefits of the cloud.