New Bill On Ransomware And What It Means For Your Business
Under the proposed bill businesses will need to inform ACSC of the attack
Ransomware is a profitable pursuit for cyber criminals and a difficult one for businesses. It is often designed to spread across a network and target database and file servers, thus paralyzing an entire organisation.
The Australian Cyber Security Centre (ACSC) saw an increase in the number of ransomware incidents against small businesses, especially over the past 18 months.
Considering the higher impact of these attacks, the Australian Government proposed a new bill. This bill makes it mandatory for organisations to report ransomware attacks to ACSC.
“The ACSC has labelled ransomware as the highest cyber threat and a significant national security threat.”
In a major attack on the Perth office of a global company, a ransom demand of $30 million was made. The attack locked its computer system in Australia, resulting in a partial interruption to online trading. These incidents are rarely one-off in the present scenario.
It is estimated that by the end of 2021, every 11 seconds a business will be targeted by a ransomware attack, causing up to $20 billion in damage.
Why Ransomware is targeting Manufacturing and Healthcare sectors
When ransomware was created, its initial victims were individual systems or individuals. However, hackers realized its full potential when they rolled out the ransomware to big businesses, especially in manufacturing and healthcare. This trend is changing again as small businesses with vulnerable defences become an easy target.
The ACSC is aware of recent ransomware campaigns targeting the aged care and healthcare sectors. These crimes view the aged care and healthcare sectors as lucrative targets for ransomware attacks. This is because of the sensitive personal and medical information they hold. A significant ransomware attack against a hospital or aged care facility would have a major impact.
Ransomware has also become a major threat to the manufacturing industry as hacker groups are increasingly taking an interest in targeting the industrial control systems (ICS) that manage operations. Research by Dargos’s cybersecurity researchers revealed that Ransomware attacks on the manufacturing sector tripled between 2019-2020.
While a lot of manufacturing relies on traditional IT, some elements of manufacturing rely on ICS. It’s an area that several hacking groups are actively looking to target. The interconnected nature of the manufacturing supply chain means wide-ranging consequences on the industry.
For instance, a ransomware attack on a medicine manufacturing facility would have an impact on the entire healthcare sector.
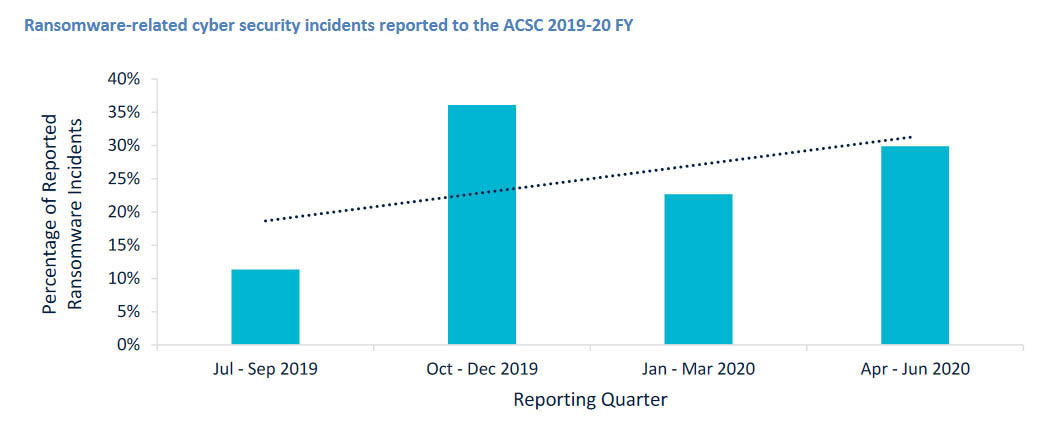
Among the top five sectors affected by ransomware reported to ACSC 2019-20, the Health sector, top it all.
Role of Managed Service Provider in defending IT infrastructure
The present figures very well state that there could a dozen more than the reported ransomware attacks happening in Australia. Hence, the govt has announced all data pertaining to the government, to be stored on onshore data centres with ‘Certified Strategic’ or ‘Certified Assured’ accreditation. The framework also requires government data to be managed by cloud and managed service providers based in Australia.
The security of cyberspace information is crucial to every enterprise or organization. Across industries, cybersecurity remains a top concern. Large businesses strive hard to implement the most effective cybersecurity risk management strategy. While small businesses have ignored them to make way for other priorities.
However, with this bill and stringent Privacy Laws in place, can you afford to ignore information security?
This is where your Managed service provider (MSP) can be of help. MSP’s IT security implementation can protect SMB’s against direct attacks and also from supply-chain related threats.

How an MSP manages Information Security
The break-fix method waits for systems, servers or other critical networking devices to fail or break to fix them. Managed services, on the other hand, seek to prevent issues prior to they can interrupt management, employees, and/or clients.
MSPs offering cybersecurity services prevent clients from falling behind in keeping up with things. They also prevent businesses from facing an IT outage or a huge issue that could impact their organisations by dealing with patches, backups, and security.
- 24×7 Network Monitoring: Your IT systems are monitored using sophisticated network monitoring tools that can easily detect anomalies in the network.
- Improved Security: With an efficient backup and disaster recovery plan, critical data can be secured and effectively recovered in the event of an attack.
- Cost-effective: Unplanned repair services can be a huge cost burden on enterprises. By hiring MSPs, enterprises succeed in controlling such costs by paying fixed monthly costs. This covers all kinds of repairs and service costs on a contractual basis.
- Comprehensive Reporting: MSPs offer a complete view of the enterprise infrastructure, helping you to be aware of your IT health.
NETCorp, for instance, offers a security solution that is integrated and has capabilities to collect and correlate deep activity data across multiple vectors – email, endpoints, servers, cloud workloads, and networks. This makes the need for multiple security solutions redundant, which directly translates into cost savings for companies. The cybersecurity application deployed by us finds incidents earlier with correlated detections and built-in threat intelligence. The present threat landscape demands a solution that goes beyond just the endpoint.
Building Cybersecurity Risk Management strategy
- Take stock of the most valuable digital assets: These includes computers, systems, networks, or data. Precise understanding is required on which of these assets are at risk and unsecured.
- Identify the risk: Identification is crucial to any risk management.
- Planning response: The cost of a data breach can be staggering. Plans help organizations and incident response teams to react quickly to attacks and contain the attack and costs.
- Review your controls: Review the controls in place to make sure they adequately cover the current risk. Continuous monitoring is important because the risk landscape is constantly changing and controls should change to effectively protect assets.
- Build a culture of cybersecurity in your organization: It’s critical to create a culture of security in your organization. Security is everyone’s job.
- Good cyber practices go a long way towards keeping an organization safe from attacks like phishing or other engineered breaches. Businesses should invest in cyber infrastructure to combat these challenges and threats than a mere warning reads.
There are steps to help protect computers and devices against being infiltrated by ransomware.
- Install reliable ransomware protection software.
- Update system up to date to safeguard from the latest malware.
- Ensure backup for data.
- Don’t pay the ransom. Even if the same paid, files might remain corrupted and trial for monetary extortion may continue without releasing those encroached data.
Other than the aforementioned, regular safety measures should be strictly adhered to.
While keeping abreast latest technologies, demands more attentive, exclusive pressure on all of our cyber resilience. There should be more focused, sustained and coordinated efforts in tracking, identifying and defending these cyber-attacks. Businesses today have more to lose from data loss than ever before. This calls for an immediate, aggressive campaign against this ransomware unlike ever before.
Safeguarding data and network needs to be prioritised, these are not the best times to risk. Get in touch and our cyber threat experts will help you set up a strong defense without creating a dent in your budget.